API key security
Using security measures, you can restrict where this API key can be used from. This way, you can prevent misuse of your key.
You can set up the security in My Account portal under the settings of individual API keys.
You can choose one of three types of API key security (it is not possible to combine them).
Attention, the security changes will not take effect immediately but gradually over about 15 minutes.
Security using HTTP referers
Specify a list of valid HTTP referers (domains/subdomains) for calls with this API key.
- Only the host and port part of the referer are validated. The protocol, path, and get parameters are ignored.
- The condition, therefore, cannot contain the
/character. - The condition can include the
*character, which represents any alphanumeric character + hyphen (basically, what a domain name can contain). For example: *.mapy.cz. The asterisk is applied only to one part of the hostname (between dots), so for *.mapy.cz, frame.mapy.cz will pass, but mapy.cz or cs.frame.mapy.cz will not. - The condition can be:
- host name
test.example.com - host name with port
test.example.com:8080 - IPv4 address
192.168.10.10 - IPv4 address with port
192.168.10.10:8080 - IPv6 address
[2001:db8::1] - IPv6 address with port
[2001:db8::1]:8080
Examples of typical settings:
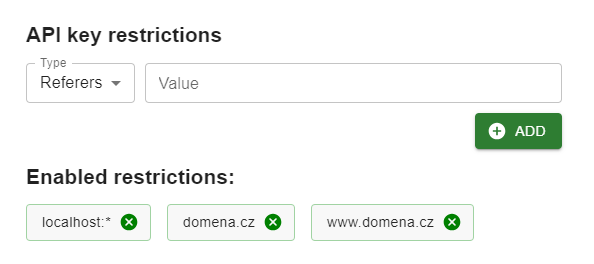
domena.cz
www.domena.cz
subdomena.domena.cz
*.domena.cz
localhost:*Security using IP addresses
Specify a list of valid IP addresses or their ranges applicable for calls made with this API key.
- IP addresses should be entered in CIDR notation.
Examples of common settings:
Single address:
172.30.2.3/32
172.30.2.3
Network/Subnet:
172.30.2.0/24Security using user-agent
Specify a list of valid user agents for calls made with this API key.
- Wildcard characters are not allowed here; we check for an exact match.
Examples of common settings:
cortex/1.0
LibreOffice
Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/106.0.0.0 Safari/537.36