API key security
API key security reduces the risk of misuse. It restricts where and for what purpose this API key can be called.
If the client is publicly accessible, such as running in a web browser, a potential attacker can easily intercept communication and use the obtained API key elsewhere. While no security measure is 100% foolproof, proper configuration significantly hinders its misuse and minimizes the risk of unauthorized access.
We offer the following security options:
- Restriction by HTTP referers – allowing only specific domains or subdomains
- Restriction by IP addresses – access only from defined IP addresses or ranges
- Restriction by User-Agent – calls allowed only with a specific client identifier
- Restriction by selected services – allowing only specific API services
We always recommend securing production API keys to minimize the risk of their misuse.
You can configure security settings in the My Account portal under individual API key settings.
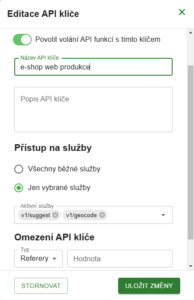
Security by selecting services
Restrict API key usage only to specific services that you actually use.
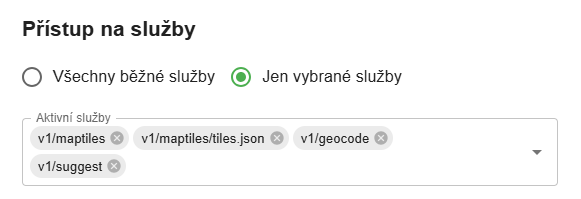
Default settings:
- The API key has access to all standard services (REST API endpoints).
How to set restrictions?
- Go to the Service Access section.
- Select the option “Only selected services”.
- Select the services that the API key is allowed to use.
- Save the settings.
You can combine this restriction with other rules, such as allowing only specific HTTP referers or IP addresses.
Note: Security changes do not take effect immediately but gradually within about 15 minutes.
Security by HTTP referers
Specify a list of valid HTTP referers (domains/subdomains) for calling with this API key.
- Only the host and port parts of the referer are validated. The protocol, path, and GET parameters are ignored.
- The condition cannot contain
/. - The condition can contain the
*character, which represents any alphanumeric character plus a hyphen (essentially what can be part of a domain name), e.g., *.mapy.cz. The asterisk applies only to one part of the hostname (between dots), so for *.mapy.cz, frame.mapy.cz will match, but mapy.cz or cs.frame.mapy.cz will not.
Examples of typical settings:
domena.cz
www.domena.cz
subdomena.domena.cz
*.domena.cz
localhost:*Security by IP addresses
Specify a list of valid IP addresses or ranges for calling with this API key.
- IP addresses are entered using CIDR notation.
Examples of typical settings:
Single address:
172.30.2.3/32
172.30.2.3
Network/Subnetwork
172.30.2.0/24Security by User-Agent
Specify a list of valid user agents for calling with this API key.
- Wildcards cannot be used; we check for an exact match.
Examples of typical settings:
cortex/1.0
LibreOffice
Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/106.0.0.0 Safari/537.36